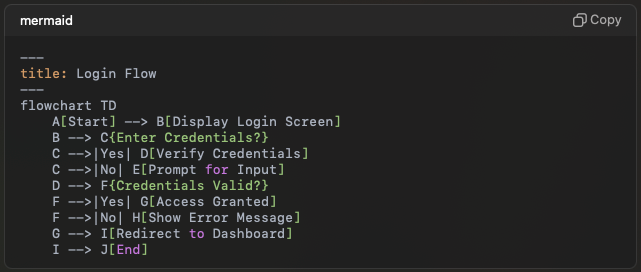
Mastering Digital Transformation: A Roadmap to Scalable and Secure IT Foundations
(16 Article Series) Introduction: Why Resilience and Compliance Matter

Hello, friends! Over my years of working in technology, I have seen businesses grapple with the challenge of creating IT systems that can grow with them while staying secure and compliant. It’s a balancing act: you want your systems to be agile enough to handle increased demand, but also robust enough to fend off threats. This article is your gateway to mastering that balance.
Welcome to the first step in a 16-part journey. Each article in this series will help you tackle specific aspects of building scalable and secure IT systems — from assessing your current infrastructure to implementing cutting-edge technologies. By the end, you’ll have a practical roadmap for success.
Section 1: The Core Pillars — Scalability and Security
Let’s start with the basics. Scalability is the ability of your IT systems to grow as your business does. Whether it is handling more users, processing larger datasets, or managing increased traffic, scalable systems adapt without breaking a sweat.
On the other hand, security is your safety net. It protects your systems from unauthorized access, data breaches, and other threats. The challenge lies in balancing these two forces — because what good is a scalable system if it is riddled with vulnerabilities?
We’ll dive into these principles in Article 1: The Blueprint of Resilient IT Systems, where I would explain how scalability and security work hand in hand to support digital transformation.
Section 2: Evaluating the Present to Shape the Future
Before you build something great, you need to know where you are starting. Infrastructure analysis helps you identify inefficiencies, bottlenecks, and vulnerabilities in your existing systems. It is a critical first step in any IT transformation.
In Article 2: Diagnosing the Present to Build the Future, we would explore how to assess your systems and identify areas for improvement. We would also discuss pinpointing inefficiencies in Article 3: Pinpointing Weak Links in Your Digital Ecosystem so you can lay the foundation for progress.
Section 3: Designing for Growth and Change
This is where strategy meets innovation. From setting SMART goals to implementing modular architectures, designing scalable IT systems requires forward-thinking decisions. It also means choosing technologies that grow with your business, like cloud-native platforms, microservices, and containerization.
In this section of the series:
- Article 4: Setting Targets That Drive Transformation will guide you through goal-setting.
- Article 5: Design Smarter, Not Harder unpacks architecture and design patterns.
- Article 6: Building the Right Stack for Growth discusses choosing the right technologies.
- Article 7: Planning for Growth Without Growing Pains simplifies capacity planning and resource allocation.
Section 4: Protecting What Matters Most
Your data and systems are among your most valuable assets, so protecting them is non-negotiable. Whether it is implementing firewalls, encrypting sensitive data, or managing access, every layer of security you add strengthens your resilience.
We will dive deep into these topics:
- Article 8: Network Security Basics You Can’t Afford to Ignore covers the fundamentals.
- Article 9: Encrypt Everything highlights best practices for data protection.
- Article 10: Who Goes There? focuses on identity and access management.
Section 5: Monitoring and Governance for Continuous Success
Building resilient IT systems does not end at implementation : you need to monitor performance, optimize for efficiency, and ensure compliance with governance standards. These practices keep your systems running smoothly and your business on track.
In this section of the series:
- Article 11: The Art of Performance Tuning explores system monitoring and optimization.
- Article 12: The Silent Guard explains how SIEM tools help detect and respond to threats.
- Article 13: Ready for the Unexpected walks you through backup and disaster recovery planning.
- Article 14: The Rules That Keep IT Safe and Efficient delves into IT governance and compliance.
Section 6: Building a Culture of Excellence
Technology is only as effective as the people behind it. Cultivating a security-first mindset, staying informed about emerging trends, and fostering a culture of learning can future-proof your IT strategies.
We’ll wrap up with these insightful topics:
- Article 15: Keep Learning, Keep Growing emphasizes the importance of continuous improvement.
- Article 16: Making Security a Habit provides strategies for embedding security into your organizational culture.
Conclusion: Your Path to IT Excellence
I hope this roadmap excites you as much as it does me. Over the next 16 articles, we will go beyond theory into actionable strategies you can implement in your business. Whether you are a seasoned tech leader or just starting your digital transformation journey, this series will empower you to build IT systems that are scalable, secure, and future-ready.
Let’s start this journey together with Article 1: The Blueprint of Resilient IT Systems. I’ll see you there!